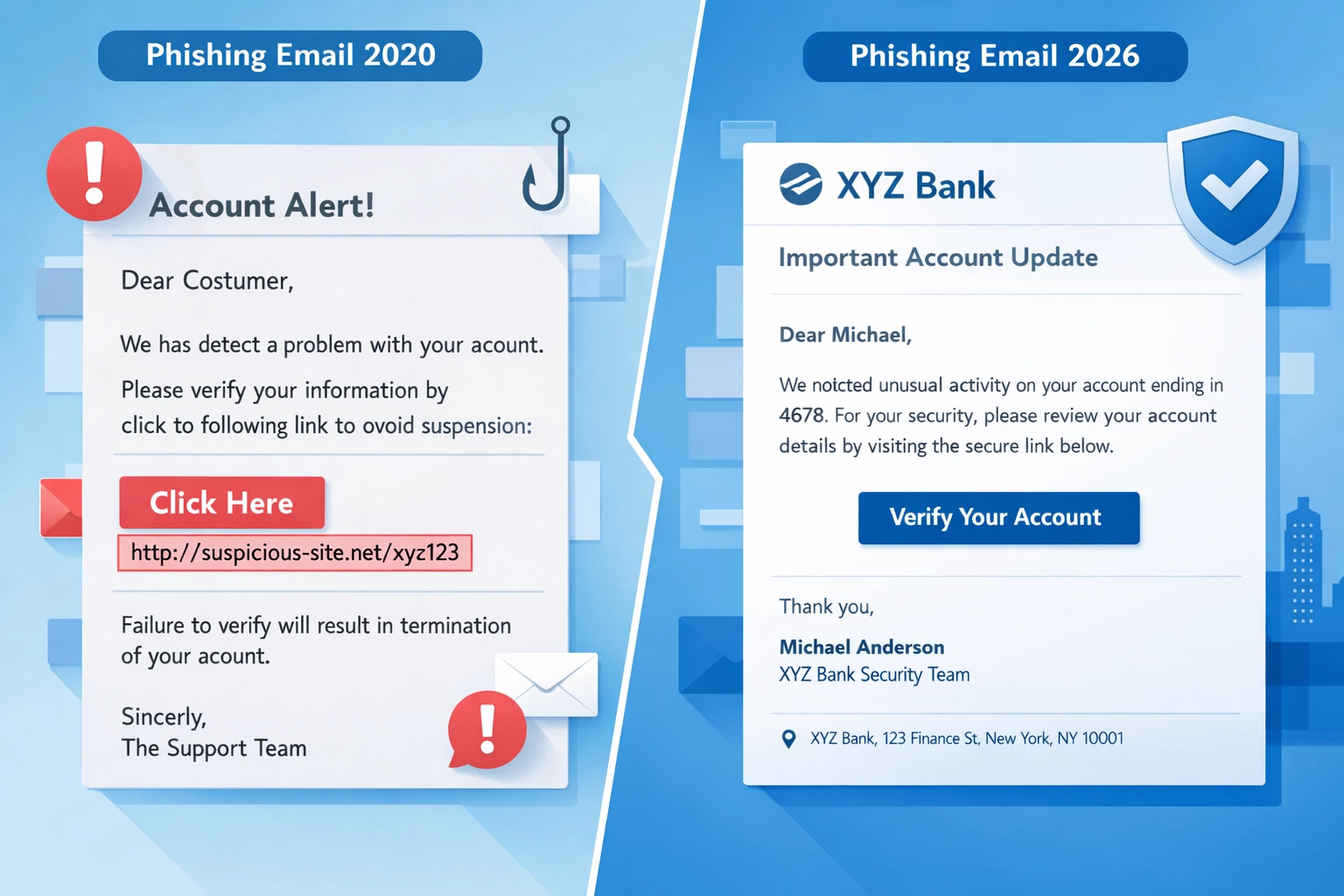
Remember when phishing emails were laughably obvious? The ones with broken English, generic greetings, and sketchy links that screamed "don't click me"? Yeah, those days are long gone.
In 2026, phishing attacks have evolved into something far more dangerous. Thanks to AI and automation, cybercriminals can now craft hyper-personalized attacks that fool even the most security-conscious employees. If your team is still looking for typos and weird sender addresses, you're not prepared for what's actually out there.
Let's talk about what modern phishing looks like and how to train your team to spot it before it causes serious damage.
The AI Revolution Made Phishing Way More Convincing
Here's a stat that should wake you up: AI-generated phishing emails have a 54% click-through rate compared to just 12% for human-written ones. That's not a typo. More than half of people who receive AI-crafted phishing emails click on them.
The reason is simple: AI can analyze social media profiles, company websites, and public databases to create messages that feel genuinely personal. It knows your job title, your recent projects, who you report to, and even your communication style. What used to take a cybercriminal 16 hours to research and craft now takes about 5 minutes with AI tools.
Over 73% of phishing emails in 2024 showed signs of AI involvement, and that number is climbing above 90% for advanced attacks. We're not just dealing with smarter individual hackers anymore: we're up against industrialized "Phishing-as-a-Service" platforms that anyone can subscribe to and launch professional-grade attacks.
It's Not Just Email Anymore
If your training program only covers email phishing, you're leaving massive gaps in your defense. Modern attackers are coming at your team from multiple directions:
Voice Phishing (Vishing) has exploded, with attacks surging 442% in recent months. Scammers are now using deepfake audio to clone executive voices and authorize fraudulent wire transfers. Imagine getting a call that sounds exactly like your CEO asking you to process an urgent payment. That's happening right now.
QR Code Phishing bypasses traditional email filters entirely. Employees scan a code thinking they're accessing a legitimate resource, but they're actually handing over credentials to attackers. These attacks are particularly effective because people tend to trust QR codes more than links.
SMS Phishing exploits the fact that people view text messages as more trustworthy than email. A quick text from "IT Support" asking you to verify your account can catch people off guard, especially when they're away from their desk.
The lesson here is clear: your team needs to be suspicious of unexpected requests across all communication channels, not just their inbox.

The New Tricks That Fool Security Systems
Attackers aren't just getting better at fooling people: they're also getting better at fooling your security tools.
Polymorphic attacks change their appearance constantly, making them harder for filters to detect. By 2024, over 76% of phishing attacks had at least one polymorphic feature. These attacks use context-aware payloads that behave normally when scanned by security bots but deploy malicious content when clicked by actual humans.
CAPTCHA abuse is becoming standard practice. By the end of 2026, more than 85% of phishing attacks are expected to use CAPTCHA screens. Why? Because employees see a CAPTCHA and think "this must be legitimate": after all, bots can't solve CAPTCHAs, right? Attackers know this and exploit that false sense of security.
MFA downgrade attacks manipulate login flows to force less secure authentication methods like SMS codes, which can be intercepted. Even if your organization requires multi-factor authentication, attackers are finding ways around it by stealing access tokens or using man-in-the-middle techniques.
What Your Training Program Needs to Cover
Generic "don't click suspicious links" training isn't cutting it anymore. Here's what your team actually needs to know:

Question Everything Personal: Just because an email references your recent project or mentions a colleague doesn't mean it's legitimate. Attackers scrape this information from LinkedIn, company websites, and social media. Train employees to verify unexpected requests through a separate, known communication channel: not by replying to the suspicious message.
Verify High-Value Requests Through Multiple Channels: Any request involving money, credentials, or sensitive data should require verification through a secondary method. If someone calls asking you to process a wire transfer, hang up and call them back at a known number. If an email asks you to reset your password, go directly to the website instead of clicking the link.
Be Skeptical of Urgency: Phishing attacks almost always create a false sense of urgency. "Your account will be locked in 24 hours." "Process this payment immediately." "Verify your credentials now." Legitimate requests rarely demand instant action without proper procedures.
Understand Authentication Risks: Employees need to know that entering credentials on unusual login screens: even if they look legitimate: can compromise accounts. Attackers now steal access tokens and relay authentication through real websites to bypass MFA. If something feels off about a login prompt, stop and verify.
Scan QR Codes Carefully: Never scan QR codes in unsolicited messages. Always verify URLs before visiting sites, and when in doubt, type the web address manually instead of scanning.
Industry-Specific Threats to Watch
Some sectors get hit harder than others. Banking and insurance account for 38% of AI phishing campaigns, healthcare and pharma take 21%, and energy and critical infrastructure face 17% of attacks.

If you work in these industries, you need specialized training for roles that handle credentials, approvals, or sensitive transactions. Finance staff, HR personnel, IT administrators, and executives are particularly valuable targets because compromising their accounts gives attackers access to high-value systems and data.
The trend is shifting from volume-based spray-and-pray attacks to highly targeted campaigns aimed at specific individuals with access to money or data. Your training needs to reflect this reality.
Making Training Actually Stick
Here's the truth: one annual training session won't cut it. Phishing techniques evolve constantly, and your team's awareness needs to keep pace.
Run simulated phishing campaigns regularly to see who's clicking and who's reporting. Don't use these as "gotcha" moments: use them as teaching opportunities. When someone falls for a simulated phish, that's not failure: that's a chance to learn without real consequences.
Keep training sessions short and frequent rather than long and annual. Ten minutes every month beats two hours once a year. Share real examples of current phishing attempts your organization has received. Nothing drives the point home like seeing an actual attack that targeted your company.
Create a culture where reporting suspicious messages is celebrated, not embarrassing. Your employees are your first line of defense, but only if they feel comfortable speaking up when something seems off.

Getting Professional Help
Look, training your team is critical, but it's only part of the solution. Modern cybersecurity requires layered defenses that combine technology, processes, and people.
If you're concerned about your organization's vulnerability to sophisticated phishing attacks, professional cybersecurity support can help identify gaps in your defenses and implement comprehensive protection strategies. From email filtering and endpoint protection to incident response planning, there are tools and services specifically designed to combat these evolving threats.
Managed IT support can also monitor your systems 24/7 for signs of compromise and respond quickly when attacks occur. Because here's the reality: even with great training, some attacks will get through. The question is whether you'll detect and contain them before they cause serious damage.
The Bottom Line
Phishing in 2026 is a completely different beast than it was even two years ago. AI-powered personalization, voice cloning, multi-channel attacks, and sophisticated evasion techniques mean your team is facing threats that are harder to spot and more convincing than ever.
The good news is that informed, vigilant employees are still your best defense. Train them on modern attack vectors, teach them to verify before they trust, and create systems that make reporting suspicious activity easy and expected.
Because the attackers are getting smarter every day. Your team needs to keep pace.

